2.2. Security¶
Fast Data Tools can be used to inspect or interact with your Kafka cluster. It is important to know how they work and how you can protect you cluster from unauthorized access. Please read this page carefully.
Contents
2.2.1. Kafka Components REST APIs¶
Kafka Topics UI, Schema Registry UI and kafka Connect UI make use of REST interfaces from Kafka - Confluent components. In their current form they are javascript based apps that run inside the browser of the user. Thus the user needs to have direct access to Kafka REST Proxy for Kafka Topics UI, to Schema Registry for Schema Registry UI and to a Connect Distributed worker for Kafka Connect UI.
Due to often misconfigured CORS settings for REST Proxy and Schema Registry, we chose to proxy them by default. Connect Distributed doesn’t support CORS headers yet, so it mandatory to proxy it.
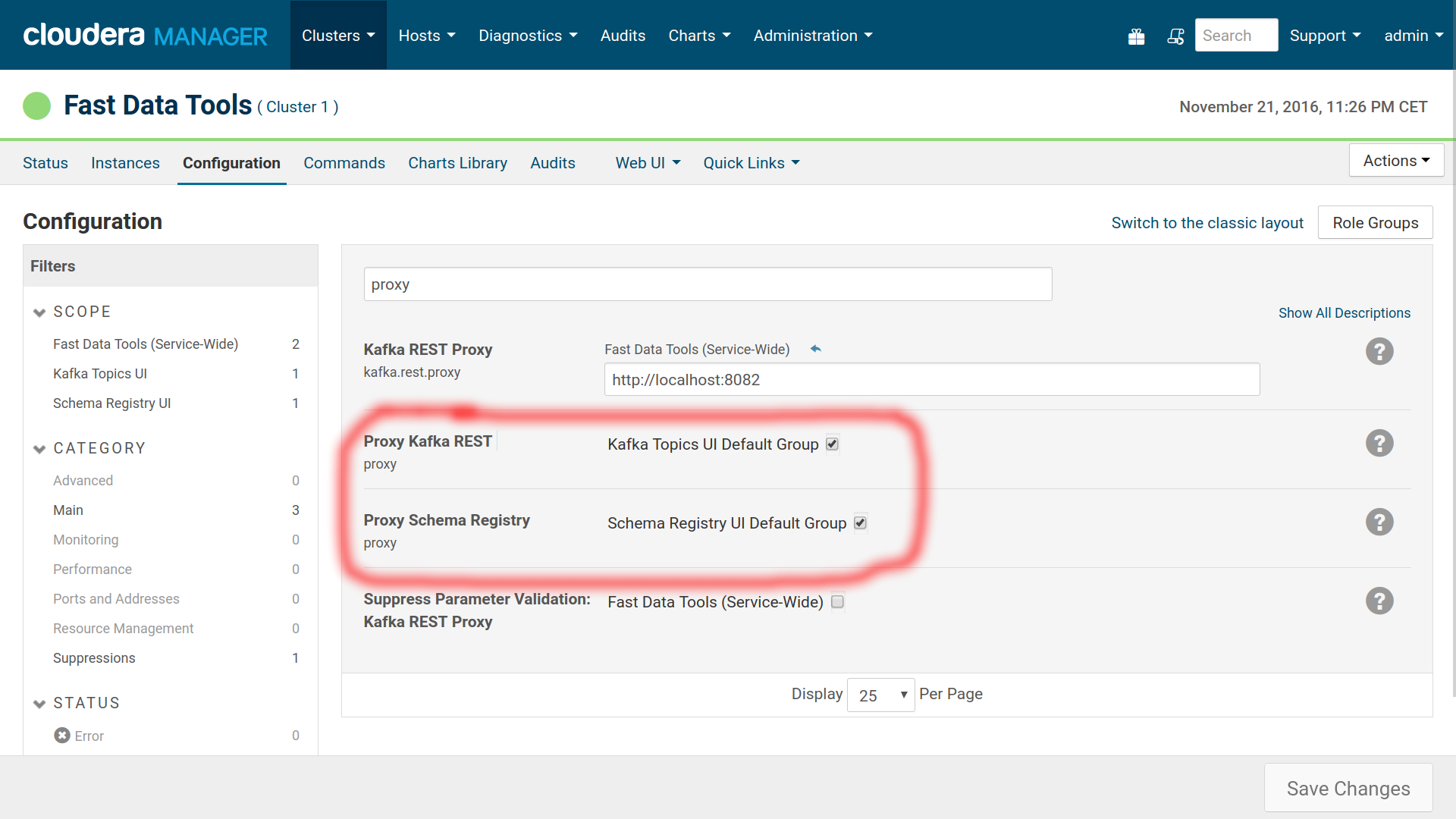
By default we proxy the REST APIs.
This means that we expose Kafka REST Proxy at port 13031, Schema Registry at port 13032 and Connect Distributed at port 13033. You should make sure these ports are secured if you want to keep the default settings.
If you prefer to access the REST APIs directly —and maybe already have some form of authentication for them—, turn off the proxy option and make sure you have configured correctly the CORS options. Unfortunately this isn’t possible for Connect Distributed.
For Schema Registry you would add these properties:
access.control.allow.methods=GET,POST,PUT,DELETE,OPTIONS
access.control.allow.origin=*
For Kafka REST Proxy:
access.control.allow.methods=GET,POST,PUT,DELETE,OPTIONS
access.control.allow.origin=*
2.2.2. Basic Authentication¶
We do offer the option to enable basic authentication for each UI. Basic authentication isn’t a very strong protection, especially in absence of SSL but can be useful. You may enable it for each role separately at the services configuration page. After changing the configuration, you need to restart the service.
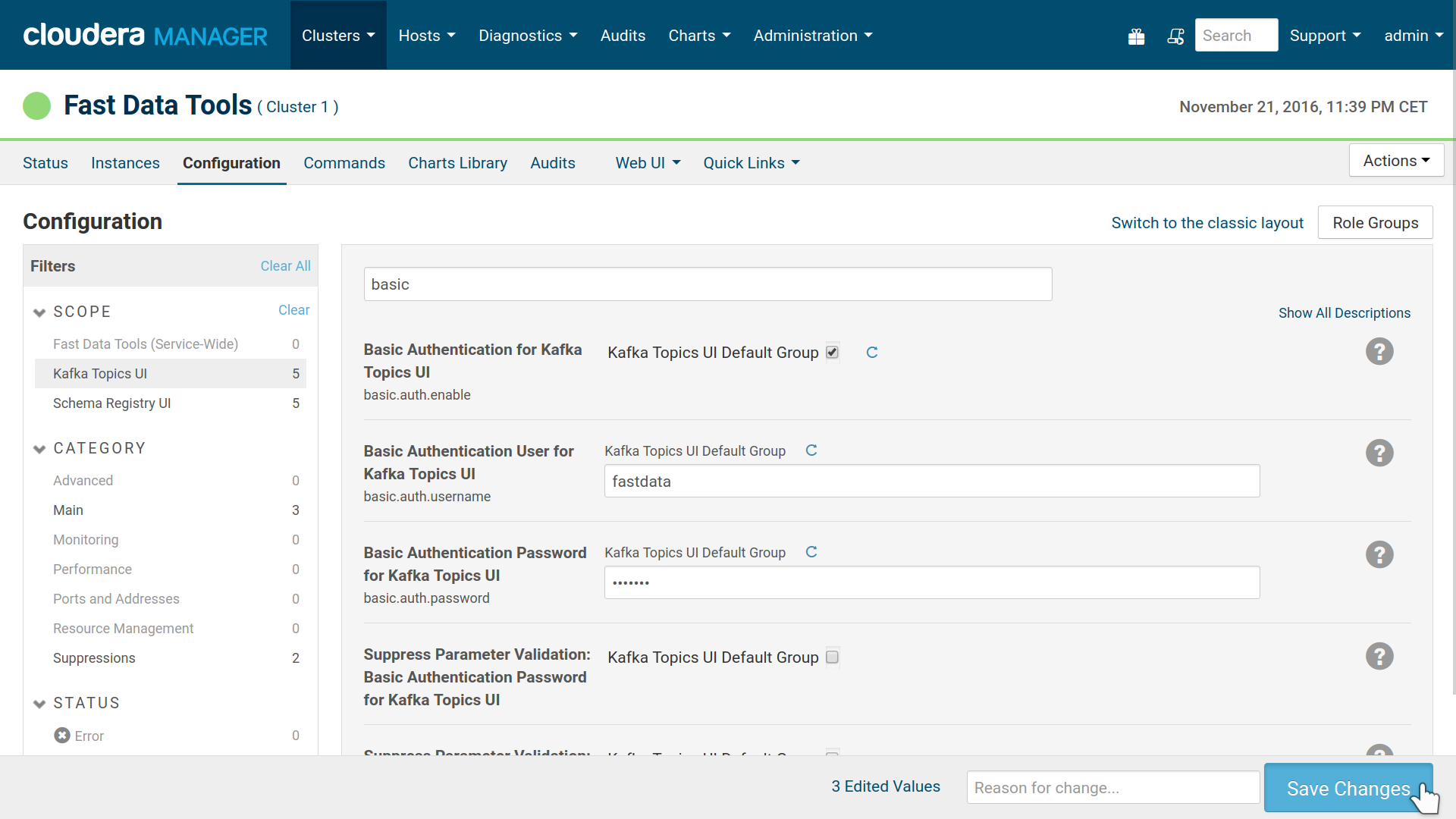
Basic Auth settings for Kafka Topics UI
2.2.3. TLS/SSL¶
TLS/SSL is implemented using Cloudera Manager’s infrastructure. In CM visit each role’s security settings to enable https. You will need a key-certificate pair in pem format.
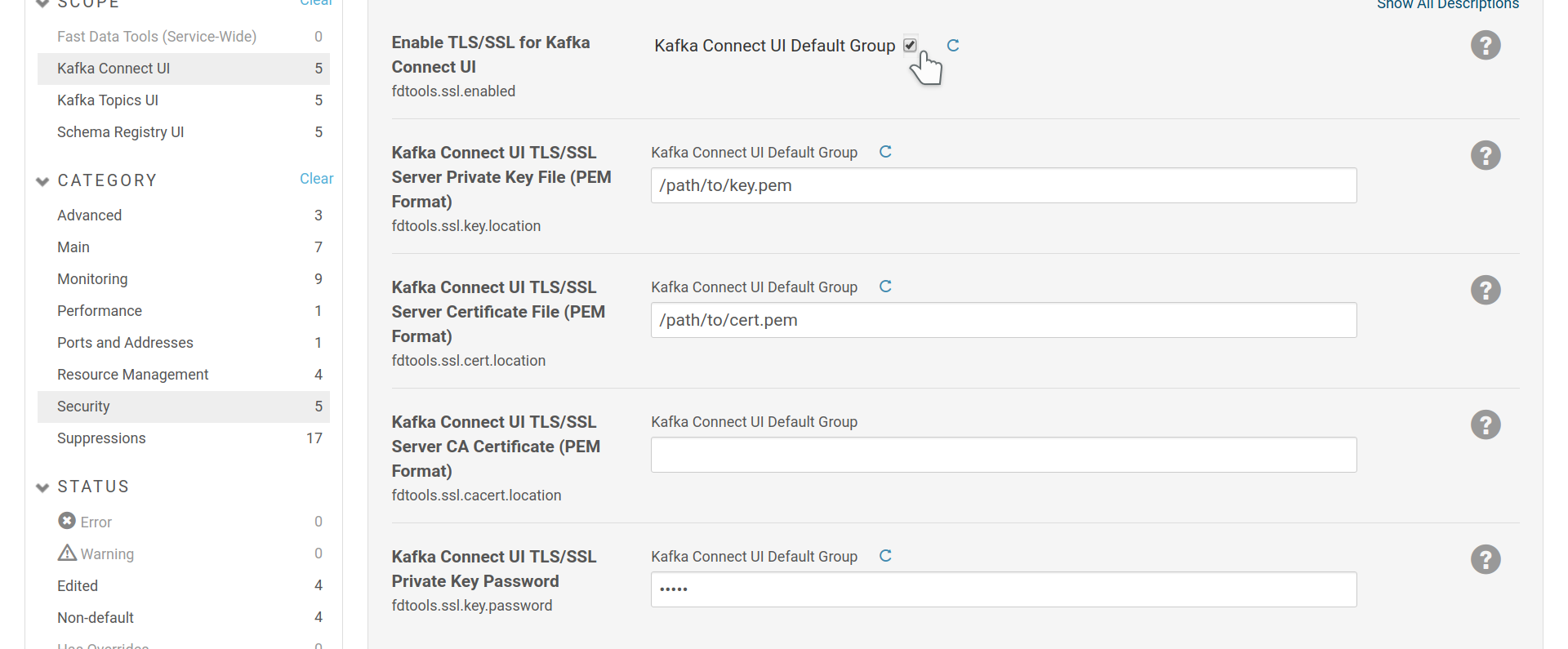
SSL configuration for Kafka Connect UI. Kafka Topics and UI and Schema Registry UI provide the same settings.
If you don’t have a password set for your private key, leave
fdtools.ssl.key.password field empty. fdtools.ssl.cacert.location field
is optional and can be set to a file containing your CA chain in PEM
format. Often the CA chain is included in the certificate itself and there is no
need to set it explicitly.
2.2.4. Authentication via Client Certificates¶
Client SSL Certificates can be used for authentication to the UIs. It is mandatory to enable TLS/SSL for the UIs before setting this type of authentication.
To enable client certificates, use the fdtools.ssl.client.auth field, as
well as the fdtools.ssl.client.cas field to provide a list of CAs you trust
to sign certificates for your clients.
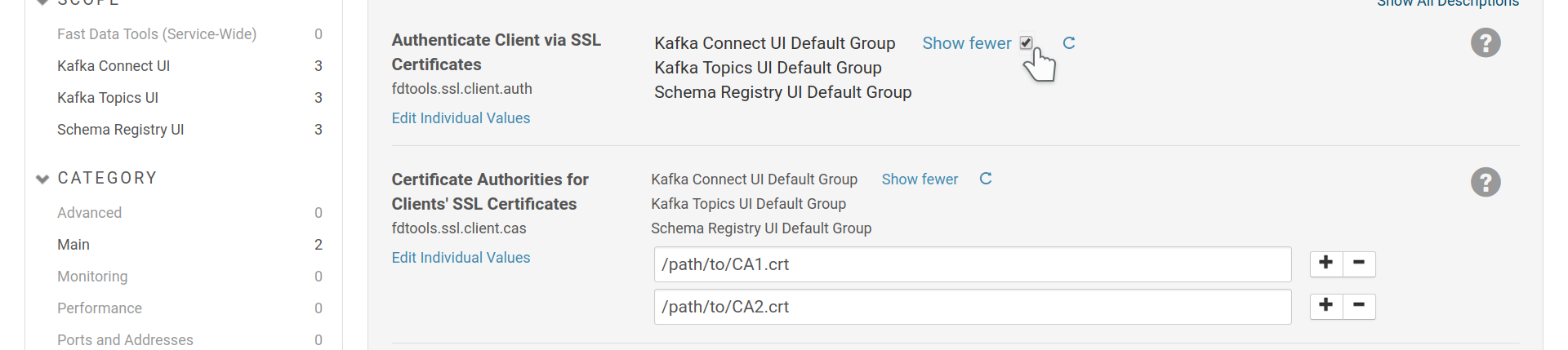
Enable authentication via client certificates for all UIs and add certificates of trusted CAs. It is possible to set these options per UI.
Once you add your client certificate to the browser and visit a UI, the browser will ask permission to use it:
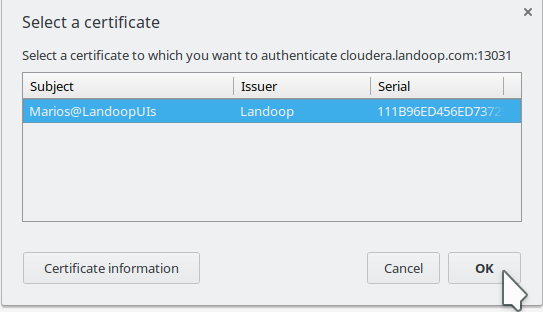
Chrome requests permission to use a client certificate to login to Kafka Topics UI.